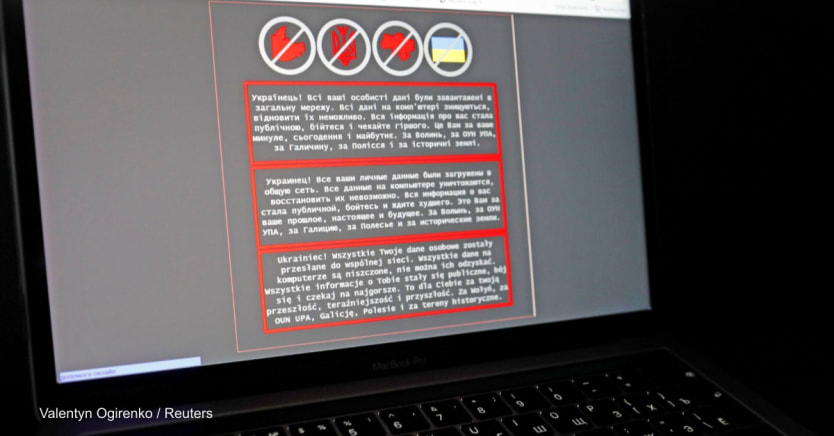
With reports that Ukraine’s critical infrastructure could already be under cyberattack by Russian government hackers, it is increasingly clear that any humanitarian response to a potential conflict between the two countries would have to contend with both the civilian fallout and the operational risks created by electronic warfare.
That requires a shift in thinking, planning, and working for aid groups that are more familiar with the devastation caused by rockets, guns, and mortars than by computers — and it’s not a shift the humanitarian sector has adequately prepared for, according to Nathaniel Raymond, an expert in human security and technology and a lecturer at Yale University.
Asked whether humanitarian organizations are at risk of being specifically targeted in the event of cyberwarfare, Raymond told Devex, “We should move forward under the assumption we already have been.”
He pointed to a recent hack of the International Committee of the Red Cross, which the organization announced last month.
According to Raymond, the ICRC hack represents a pivotal — but predictable — moment in the escalation of cyberthreats facing humanitarian agencies and “should be seen as a harbinger of things to come in the conflict we may be about to enter this week.”
ICRC has not determined who carried out the hack, which compromised personal data of 515,000 people from servers that contained information relating to the International Red Cross and Red Crescent Movement's Restoring Family Links services, which assist people separated from family members by conflict or disaster. Massimo Marelli, the organization’s head of data protection, told Devex earlier this month that the hack was “highly sophisticated and targeted” and compatible with a “state-like” operation.
According to Raymond, the perpetrators of the hack may never be known, but it still represents a turning point in the history of humanitarian data protection.
“I can't overstate that this ICRC hack, regardless of attribution and regardless of intention — which may never be known in both cases — represents the fundamental ‘Pearl Harbor’ moment in humanitarian data protection,” he said.
Raymond said that he has been warning for 10 years that this day would come. “And what I mean by ‘this day’ is not that we — the humanitarian community — got hacked; it's that we know about it,” he said.
Full disclosure
On Wednesday, ICRC published an update with more details about the hack.
Those whose data was compromised include “missing people and their families, detainees and other people receiving services from the Red Cross and Red Crescent Movement as a result of armed conflict, natural disasters or migration.”
“We do not believe it is in the best interest of the people whose data this is to share further details about who they are, where they are or where they came from,” ICRC wrote.
The organization has also not made contact with any perpetrators of the hack, but it offered to engage with them.
“In line with our standing practice to engage with any actor who can facilitate or impede our humanitarian work, we are willing to communicate directly and confidentially with whoever may be responsible for this operation to impress upon them the need to respect our humanitarian action,” ICRC wrote.
The hack was discovered Jan. 18, but an analysis showed that the breach occurred Nov. 9, according to ICRC. The organization said discovering the “anomaly in our system” within 70 days was significantly faster than the average of 212 days for similarly large and complex hacks — a figure it attributes to IBM's 2021 “Cost of a Data Breach Report.”
Still, ICRC’s analysis concludes the hackers were “inside” the organization’s systems with the capacity to copy and export data contained there.
At the quadrennial review of the Geneva Conventions in 2019, International Red Cross and Red Crescent Movement delegates pushed for humanitarian data protections. The negotiations specifically addressed the “family links” data that aid groups gather about people separated by conflict and disaster.
"The profiling and traceability of people who might be of interest to parties to a conflict is something that is highly problematic," ICRC’s Marelli told Agence France-Presse at the time.
According to AFP’s report, the United States opposed language formally committing states to not request access to Red Cross data "for purposes incompatible with the solely humanitarian nature of the work of the movement," and the final text was ultimately watered down.
Two years later, the same data was allegedly hacked in a “state-like” operation.
“Humanitarians, uniquely, have highly actionable intelligence about the most vulnerable populations . … Intelligence services can find that very useful to collect.”
— Nathaniel Raymond, lecturer, Yale UniversityFour big cyberwarfare risks
As tensions continue to mount between Russia and Ukraine, Raymond said four main categories of cyber risk are currently faced by civilians and the agencies that seek to assist them.
First is the potential impact of “cyberkinetic attacks on infrastructure within Ukraine,” he said. “Most notably, the heat could get knocked out.”
That means aid groups should have contingency plans for the humanitarian effects of losing basic services in the middle of the Ukrainian winter. Other attacks on physical infrastructure, such as gas pipelines, could cause direct casualties, and aid groups should know in advance what those logistical infrastructure targets could be.
The second category is “cyberinformatic” and includes attempts to “weaponize the information space,” Raymond said. The goal could be to use misinformation, disinformation, and hate speech to incite violence in Ukrainian society or to “deny humanitarian actors the protections of their status by questioning their status.”
The third category is “direct data breach on responding organizations,” as ICRC said occurred in its hack. For Raymond, the scariest thing about potential “state-like” targeting of the digital infrastructure of humanitarian groups responding in Ukraine is that it could happen without organizations knowing it.
This could mean that hackers “attack the systems and sit there” with ongoing access to information about operations and personnel.
“Humanitarians, uniquely, have highly actionable intelligence about the most vulnerable populations on the worst day of their lives, and intelligence services can find that very useful to collect in real time,” Raymond said.
The fourth category of risk is that a “sophisticated cyberactor” might seek to “deny humanitarian organizations the operational space and capability to conduct operations on the ground in Ukraine” by targeting the things they rely on to do their work. That could include financial transactions, data, personnel records, or the internet — and it could target systems in Ukraine or at headquarters.
“So those are the big four. We have to be ready for all of them, and we're frankly ready for none of them,” Raymond said.
The social-digital terrain
The reason that humanitarian groups and the populations they serve are increasingly vulnerable to cyberattacks is that these organizations have made their own operations part of the “social-digital terrain,” Raymond said.
That started when the UN Refugee Agency began collecting biometric data on its clients in 2002, Raymond said, describing this as the “Big Bang moment” in which agencies became part of the digital ecosystem.
“In this process of making civilians digitally legible, it means that our value as targets of cyberinformatic warfare has gone up exponentially and will only continue to rise,” he said.
Now, as could be the case in Ukraine, conflict also increasingly inhabits that digital ecosystem, but aid groups have not fully grappled with what that means. To get ready, humanitarian groups need to act at both a sectoral level and a country-specific level.
Asked what he would do if he were the country director for a humanitarian organization in Ukraine right now, Raymond said he would be “surging support” to that country program, including by bringing in private sector experts in areas such as civilian infrastructure.
“This ICRC hack … represents the fundamental ‘Pearl Harbor’ moment in humanitarian data protection.”
— Nathaniel Raymond, lecturer, Yale University“Frankly, the whole humanitarian community right now should be doing scenario planning [immediately] for what a multidimensional, multispectrum cyberkinetic and cyberinformatic layered attack is going to look like by the end of the week. And maybe we have that long,” he said.
At a broader level, Raymond said ICRC and other organizations that uphold humanitarian norms should clearly state that the Geneva Conventions already prohibit three things: cyberkinetic attacks on infrastructure; targeting humanitarian data, which he said should be treated the same as hospitals or humanitarian vehicles; and incitement to violence through weaponization of the information space.
“ICRC and the whole Red Cross family, the whole humanitarian family, needs to, with one voice, say: ‘Information is aid. Aid is protected. The means of collecting and transmitting that information as aid shall be treated equal to humanitarian infrastructure of a physical character,’” he said. “And that hasn't happened.”
Search for articles
Most Read
- 1
- 2
- 3
- 4
- 5








